Tuesday, December 27, 2005
Joining the Union
In anticipation of a rough and tumble year in the IT industry, today I applied via email to join Cosatu. Viva!

Friday, December 23, 2005
Slyck Interviews the MPAA
Without compromising our position on P2P, we took the view that perhaps it was time we heard what the MPAA had to say for themselves instead of only reading their views in court submissions.
read more | digg story
read more | digg story
Thursday, December 22, 2005
File Sharing Dangers
Can you spot the errors in this article? Do you think everything it says is true?
Introduction
So you have decided to join the ranks of other Internet users who share files. There is much for you to learn and understand. First understand there are many risks to what you are doing. Files you download from others can contain viruses and other nasty things. So be sure to have a good anti-virus application installed, certainly if you have a Windows-based system. Besides the risks of viruses and such, there are other risks, such as hackers and groups that monitor the internet. Understand that there are many unsafe ways to share files. Including but not limited to P2P, IRC, newsgroups and websites. There are also safe ways to share files as well.
For every connection to the internet there is assigned a unique number, called an IP address. There is no way to hide it, there is always a trail and plenty of ways to record and trace connections. There are methods of mucking up such trails and making it harder to match IP addresses. However they are usually very weak and offer little to no real protection from being traced.
Why share files?
An easy enough question to answer and understand. So that you can distributed and download content freely without paying money for it. Not that it is ever truly free, there is the cost of network bandwidth and system resources, along with the power and internet access costs. Also it can be for social reasons, such as to gain friends and access content you normally would not think to or could not easily get to otherwise. For such reasons file-sharing is very popular with millions worldwide engaging in it.
Scams
There are many bad people out there running scams, they offer access to networks and content, usually charging monthly or yearly rates for it. Granted there are legal services which do exist such as iTunes, eMusic and Audible. However there are also many scams, which upon being paid may give download access to a client, which a free and clean copy could be found elsewhere, usually at the original authors website. Such clients downloaded from the scam websites may be infected with viruses, dialers and other such nasty things. Nasty things like those with damage your system and misuse it, can even get you into trouble with the law. Such scams will lure people into unwittingly conducting content piracy, which they think is legal because they are paying for it. They will still get sued and can face time in jail, even if they were setup by a scam. Just because they were clueless does not make them safe. Anti piracy groups are usually totally heartless and courts usually will side with them if matters go that far, on the rare chance they cases make it to a jury trial, defendants are very likely to lose.
The Law
Beyond what was stated elsewhere in this FAQ, there is not much more to say. Just that understanding your local laws is a good thing if you intend to do any file-sharing. Also that regardless of any such understanding, it is not unusual to be burned by your court system, even if you did not commit a crime.
Set Up and/or Framed
So you think that you have been set up and/or framed. However wrong that may be, you should know often file-sharers are very weak and vulnerable. No matter what the circumstances that lead to you getting into trouble with the law, you are most likely to lose. Sure if you are wealthy and manage to get a very good lawyer who has a good understanding of the law, given enough time and money you can fight the charges, possibly even eventually win the case, though you must also understand you still end up losing in what you have had to spend on lawyer fees and time. File-sharers tend not to be wealthy, so there is not much need to any further along these lines.
Clients
There are many different file-sharing clients, which each offer different features and methods of networking users together. Most of which are unsafe and their users frequently tend to get into legal trouble for using them. Among the most dangerous are the P2P file-sharing clients, which usually allow direct insecure connections between file-sharers, all information concerning file-sharing is easily matched to IP addresses and file-sharers usually are left very open. A few such clients include but are not limited to LimeWire, BearShare, eMule, Morpheus, shareaza, directconnect and BitTorrent.
There are a few safe clients and methods for file-sharing, none of which connect to the internet directly. They go through overlay networks. Overlay networks are networks which exist on top of the internet. They use secure routed networking to route data between sources and destinations. They are general networks in that they are not designed specifically for file-sharing. Two such networks are tor and I2P. Tor is a very limited weak outproxy network that allows for simple web browsing and little else. So it doesn't do file-sharers much good to try abusing it. The other better developed network I2P, is more interesting and useful to file-sharers. Unlike tor it is robust and strong, but with extremely limited outproxying. Instead, members of the network have several safe options for sharing files, including serving them up on websites and with special file-sharing clients. Two such types of clients include certain Gnutella and BitTorrent clients, which have been modified to work on top of the I2P network. They offer safe file-sharing with decent speeds. Transfers and content shared using these modified clients are extremely hard to match to IP addresses, thus are safe enough for average file-sharing of most content.
Of course there are other far less safe but more lightweight and simple clients, which are safer than P2P clients. They use onion routing to make linking IP addresses to specific content hard. However they still link IP addresses directly to file-sharing, though not exposing which content the addresses were responsible for sharing.
Safety
So while sharing content through clients and networks, you should ask yourself is it safe for you to do so with the software and networking that you are using? Are you at risk and is it more than you are willing to handle?
Content and The Scene
There are many types of shared content, both legal and otherwise. Much of the more popular content is considered to be scene content. The scene is often considered as copyrighted music, movies, TV shows, software, warez and anyone sharing such content are usually tagged as pirates. Pirates which are caught, can and often are heavily fined, some may even end up spending time in jail, for the "crime" of illegal file-sharing. If you intend on sharing scene content, unsafe file-sharing is highly recommended against, it is highly risky and sooner or later you will be caught. While of course you are not encouraged to engage in illegal file-sharing by the author of this FAQ, laying out much of the facts the author knows concerning such matters is good for the FAQ's readers. For both law abiding file sharers and pirates alike.
Legal content, since illegal content was already briefly mentioned, next we will point out the less popular legal content, which should be safe to share no matter what methods and clients you use to do so. While sharing such content should be safe, it may not be allowed by your internet service provider and if certain methods are detected, some people have already lost their connections for using them. Worse more people in the future will likely also lose their connections over using file-sharing, even for use which is allowed by their local legal systems. So understand that using unsafe file-sharing can result in losing your internet connection, even if you were not breaking the law by doing so.
So just what is legal content? Legal content is the kind with licenses such as freeware, shareware, demos, trialware, public domain, GPL and LGPL. Homemade contents such as pictures, movies and personal documents are also considered legal, as long as they were originally shared by their authors and artists.
Security Measures
Some file-sharers resort to taking security measures in the hopes of protecting themselves. Such measures include but are not limited to certain client settings, filter applications such as peergaurdian, protowall, both of which use IP block lists to blacklist IP addresses which are suspected to belong to bad peers. Also content filters which block content that is supposed to be bad, either fake, infected by viruses or something along those lines.
Most such measures are limited and weak at least when it comes to the unsafe file-sharing clients and networking. Yet they can help reduce but not totally eliminate exposure to such peers and content.
I2P
Just to make some things clear concerning I2P. First it is not a file-sharing network and application. It is a general purpose network and application for freedom and privacy. No matter what is stated on the official website, forums and by developers, it is ready for large scale use, at the very least by people that are tech savvy. Which largely tends to fall into the age ranges of 30's and under.
That said, it is important to understand the risks of running it, the kind of networking and security it uses. However it is also important to realize that for the average internet user it is safe enough and provides more than enough security already to meet their needs. Just do not expect to use it as providing a haven for paedophiles and pedographic content, that the networks peers are very likely to gang up on anyone that does such things and attempt to turn your information over to the authorities. Note that the term attempt was used, because it is extremely hard to 100 percent prove a peer is the source for such content. Still the networks peers can certainly point authorities in the correct direction to a possible number of addresses they think the content provider may be from and for the authorities to start their investigation with. Though just know that peers are very unlikely to provide the authorities help against each other for other reasons. As many of them do not want to see the network become a haven for pedographic content and thus tarnish the network and projects reputation. So just know while it does help provide and protect a great amount of freedom, for the most part it is within reason. Not something which terrorists and paedophiles are welcomed to use, they should stick to abusing freenet as they have been doing.
Also there is much to I2P beyond the file-sharing clients that have been ported to it. There is real time chat, email, nntp news, websites, forums and other such common applications. Mostly 100 percent legal uses, which peers most commonly use the network for. So just because someone is running I2P does not mean they are likely using it for illegal or even questionable purposes. How much less likely, well nowhere near as likely as the P2P networks, certainly not anywhere close to as likely as freenet. So it should be legally safe to be a I2P peer at least in most areas of the world that have freedom and democracy. Such as America, Canada, Europe, Australia and Japan. As the network grows larger so will the peers safety.
Safety aside, as long as I2P's version is below 1.0 just know that there are bound to be things like bugs and a general lack of documentation, harder to configure and use, though that does not mean you cannot or should not use it. Just that it is still under heavy development and not to demand too much from it and it's developers just yet. If you are bright and willing to spend the time and effort in installing and configuring I2P and its clients, beyond that on a day to day basis it is very little if any time and effort to maintain and use. It is not yet something for the clueless unlike Kazaa and P2P clients are.
Related Sites
There are many such sites, too many to bother listing. A few such websites are
http://eff.org http://planetpeer.de http://www.slyck.com http://www.i2p.net
It is important to note, like everything which is on the internet, not all information found on a website is certain to be completely accurate and unbiased. For example slyck's forums have many posts which can be misleading, total lies and certainly biased towards P2P. You are advised against just taking much of what is on such forums as the complete truth.
The Future
No matter what the future may hold for file-sharing, such as new software and other technology. There is bound to be worse problems with shared content and bad peers, ligitious groups like the RIAA and MPAA, more file-sharers being sued and more. Sure there are safe options available now, which all file-sharers are highly recommended to use instead of the older unsafe options. You can be safe now if you take the time and put in the effort to be. Your own safety is your sole responsibility, you can ignore this FAQ's advice and continue to use unsafe file-sharing clients and networking, it is your choice to stay vulnerable or not.
The future of file-sharing is being built now, the software and networks which will become mainstream for the next five or more years are just being setup and adopted. The older type software and networks are already played out and degrading, even if they continue to grow with more new clueless users.
You do not have to join the ranks of the clueless, such as people who use Kazaa and other such vulnerable P2P. You can choose to show leadership and concern for other file-sharers well being, by adopting the safe software and networks now.

Also visit the File Sharing FAQ at DSL Reports. Download the above inaccurate information in a badly written FSFAQ as a PDF file.
Introduction
So you have decided to join the ranks of other Internet users who share files. There is much for you to learn and understand. First understand there are many risks to what you are doing. Files you download from others can contain viruses and other nasty things. So be sure to have a good anti-virus application installed, certainly if you have a Windows-based system. Besides the risks of viruses and such, there are other risks, such as hackers and groups that monitor the internet. Understand that there are many unsafe ways to share files. Including but not limited to P2P, IRC, newsgroups and websites. There are also safe ways to share files as well.
For every connection to the internet there is assigned a unique number, called an IP address. There is no way to hide it, there is always a trail and plenty of ways to record and trace connections. There are methods of mucking up such trails and making it harder to match IP addresses. However they are usually very weak and offer little to no real protection from being traced.
Why share files?
An easy enough question to answer and understand. So that you can distributed and download content freely without paying money for it. Not that it is ever truly free, there is the cost of network bandwidth and system resources, along with the power and internet access costs. Also it can be for social reasons, such as to gain friends and access content you normally would not think to or could not easily get to otherwise. For such reasons file-sharing is very popular with millions worldwide engaging in it.
Scams
There are many bad people out there running scams, they offer access to networks and content, usually charging monthly or yearly rates for it. Granted there are legal services which do exist such as iTunes, eMusic and Audible. However there are also many scams, which upon being paid may give download access to a client, which a free and clean copy could be found elsewhere, usually at the original authors website. Such clients downloaded from the scam websites may be infected with viruses, dialers and other such nasty things. Nasty things like those with damage your system and misuse it, can even get you into trouble with the law. Such scams will lure people into unwittingly conducting content piracy, which they think is legal because they are paying for it. They will still get sued and can face time in jail, even if they were setup by a scam. Just because they were clueless does not make them safe. Anti piracy groups are usually totally heartless and courts usually will side with them if matters go that far, on the rare chance they cases make it to a jury trial, defendants are very likely to lose.
The Law
Beyond what was stated elsewhere in this FAQ, there is not much more to say. Just that understanding your local laws is a good thing if you intend to do any file-sharing. Also that regardless of any such understanding, it is not unusual to be burned by your court system, even if you did not commit a crime.
Set Up and/or Framed
So you think that you have been set up and/or framed. However wrong that may be, you should know often file-sharers are very weak and vulnerable. No matter what the circumstances that lead to you getting into trouble with the law, you are most likely to lose. Sure if you are wealthy and manage to get a very good lawyer who has a good understanding of the law, given enough time and money you can fight the charges, possibly even eventually win the case, though you must also understand you still end up losing in what you have had to spend on lawyer fees and time. File-sharers tend not to be wealthy, so there is not much need to any further along these lines.
Clients
There are many different file-sharing clients, which each offer different features and methods of networking users together. Most of which are unsafe and their users frequently tend to get into legal trouble for using them. Among the most dangerous are the P2P file-sharing clients, which usually allow direct insecure connections between file-sharers, all information concerning file-sharing is easily matched to IP addresses and file-sharers usually are left very open. A few such clients include but are not limited to LimeWire, BearShare, eMule, Morpheus, shareaza, directconnect and BitTorrent.
There are a few safe clients and methods for file-sharing, none of which connect to the internet directly. They go through overlay networks. Overlay networks are networks which exist on top of the internet. They use secure routed networking to route data between sources and destinations. They are general networks in that they are not designed specifically for file-sharing. Two such networks are tor and I2P. Tor is a very limited weak outproxy network that allows for simple web browsing and little else. So it doesn't do file-sharers much good to try abusing it. The other better developed network I2P, is more interesting and useful to file-sharers. Unlike tor it is robust and strong, but with extremely limited outproxying. Instead, members of the network have several safe options for sharing files, including serving them up on websites and with special file-sharing clients. Two such types of clients include certain Gnutella and BitTorrent clients, which have been modified to work on top of the I2P network. They offer safe file-sharing with decent speeds. Transfers and content shared using these modified clients are extremely hard to match to IP addresses, thus are safe enough for average file-sharing of most content.
Of course there are other far less safe but more lightweight and simple clients, which are safer than P2P clients. They use onion routing to make linking IP addresses to specific content hard. However they still link IP addresses directly to file-sharing, though not exposing which content the addresses were responsible for sharing.
Safety
So while sharing content through clients and networks, you should ask yourself is it safe for you to do so with the software and networking that you are using? Are you at risk and is it more than you are willing to handle?
Content and The Scene
There are many types of shared content, both legal and otherwise. Much of the more popular content is considered to be scene content. The scene is often considered as copyrighted music, movies, TV shows, software, warez and anyone sharing such content are usually tagged as pirates. Pirates which are caught, can and often are heavily fined, some may even end up spending time in jail, for the "crime" of illegal file-sharing. If you intend on sharing scene content, unsafe file-sharing is highly recommended against, it is highly risky and sooner or later you will be caught. While of course you are not encouraged to engage in illegal file-sharing by the author of this FAQ, laying out much of the facts the author knows concerning such matters is good for the FAQ's readers. For both law abiding file sharers and pirates alike.
Legal content, since illegal content was already briefly mentioned, next we will point out the less popular legal content, which should be safe to share no matter what methods and clients you use to do so. While sharing such content should be safe, it may not be allowed by your internet service provider and if certain methods are detected, some people have already lost their connections for using them. Worse more people in the future will likely also lose their connections over using file-sharing, even for use which is allowed by their local legal systems. So understand that using unsafe file-sharing can result in losing your internet connection, even if you were not breaking the law by doing so.
So just what is legal content? Legal content is the kind with licenses such as freeware, shareware, demos, trialware, public domain, GPL and LGPL. Homemade contents such as pictures, movies and personal documents are also considered legal, as long as they were originally shared by their authors and artists.
Security Measures
Some file-sharers resort to taking security measures in the hopes of protecting themselves. Such measures include but are not limited to certain client settings, filter applications such as peergaurdian, protowall, both of which use IP block lists to blacklist IP addresses which are suspected to belong to bad peers. Also content filters which block content that is supposed to be bad, either fake, infected by viruses or something along those lines.
Most such measures are limited and weak at least when it comes to the unsafe file-sharing clients and networking. Yet they can help reduce but not totally eliminate exposure to such peers and content.
I2P
Just to make some things clear concerning I2P. First it is not a file-sharing network and application. It is a general purpose network and application for freedom and privacy. No matter what is stated on the official website, forums and by developers, it is ready for large scale use, at the very least by people that are tech savvy. Which largely tends to fall into the age ranges of 30's and under.
That said, it is important to understand the risks of running it, the kind of networking and security it uses. However it is also important to realize that for the average internet user it is safe enough and provides more than enough security already to meet their needs. Just do not expect to use it as providing a haven for paedophiles and pedographic content, that the networks peers are very likely to gang up on anyone that does such things and attempt to turn your information over to the authorities. Note that the term attempt was used, because it is extremely hard to 100 percent prove a peer is the source for such content. Still the networks peers can certainly point authorities in the correct direction to a possible number of addresses they think the content provider may be from and for the authorities to start their investigation with. Though just know that peers are very unlikely to provide the authorities help against each other for other reasons. As many of them do not want to see the network become a haven for pedographic content and thus tarnish the network and projects reputation. So just know while it does help provide and protect a great amount of freedom, for the most part it is within reason. Not something which terrorists and paedophiles are welcomed to use, they should stick to abusing freenet as they have been doing.
Also there is much to I2P beyond the file-sharing clients that have been ported to it. There is real time chat, email, nntp news, websites, forums and other such common applications. Mostly 100 percent legal uses, which peers most commonly use the network for. So just because someone is running I2P does not mean they are likely using it for illegal or even questionable purposes. How much less likely, well nowhere near as likely as the P2P networks, certainly not anywhere close to as likely as freenet. So it should be legally safe to be a I2P peer at least in most areas of the world that have freedom and democracy. Such as America, Canada, Europe, Australia and Japan. As the network grows larger so will the peers safety.
Safety aside, as long as I2P's version is below 1.0 just know that there are bound to be things like bugs and a general lack of documentation, harder to configure and use, though that does not mean you cannot or should not use it. Just that it is still under heavy development and not to demand too much from it and it's developers just yet. If you are bright and willing to spend the time and effort in installing and configuring I2P and its clients, beyond that on a day to day basis it is very little if any time and effort to maintain and use. It is not yet something for the clueless unlike Kazaa and P2P clients are.
Related Sites
There are many such sites, too many to bother listing. A few such websites are
http://eff.org http://planetpeer.de http://www.slyck.com http://www.i2p.net
It is important to note, like everything which is on the internet, not all information found on a website is certain to be completely accurate and unbiased. For example slyck's forums have many posts which can be misleading, total lies and certainly biased towards P2P. You are advised against just taking much of what is on such forums as the complete truth.
The Future
No matter what the future may hold for file-sharing, such as new software and other technology. There is bound to be worse problems with shared content and bad peers, ligitious groups like the RIAA and MPAA, more file-sharers being sued and more. Sure there are safe options available now, which all file-sharers are highly recommended to use instead of the older unsafe options. You can be safe now if you take the time and put in the effort to be. Your own safety is your sole responsibility, you can ignore this FAQ's advice and continue to use unsafe file-sharing clients and networking, it is your choice to stay vulnerable or not.
The future of file-sharing is being built now, the software and networks which will become mainstream for the next five or more years are just being setup and adopted. The older type software and networks are already played out and degrading, even if they continue to grow with more new clueless users.
You do not have to join the ranks of the clueless, such as people who use Kazaa and other such vulnerable P2P. You can choose to show leadership and concern for other file-sharers well being, by adopting the safe software and networks now.

Also visit the File Sharing FAQ at DSL Reports. Download the above inaccurate information in a badly written FSFAQ as a PDF file.
Wednesday, December 21, 2005
RIAA bans telling friends about new songs
November 30, 2005, LOS ANGELES
 The Recording Industry Association of America announced Tuesday that it will be taking legal action against anyone discovered telling friends, acquaintances, or associates about new songs, artists, or albums. "We are merely exercising our right to defend our intellectual properties from unauthorized peer-to-peer notification of the existence of copyrighted material," a press release signed by RIAA anti-piracy director Brad Buckles read.
The Recording Industry Association of America announced Tuesday that it will be taking legal action against anyone discovered telling friends, acquaintances, or associates about new songs, artists, or albums. "We are merely exercising our right to defend our intellectual properties from unauthorized peer-to-peer notification of the existence of copyrighted material," a press release signed by RIAA anti-piracy director Brad Buckles read.
 "We will aggressively prosecute those individuals who attempt to pirate our property by generating 'buzz' about any proprietary music, movies, or software, or enjoy same in the company of anyone other than themselves." RIAA attorneys said they were also looking into the legality of word-of-mouth "favorites-sharing" sites, such as coffee shops, universities, and living rooms.
"We will aggressively prosecute those individuals who attempt to pirate our property by generating 'buzz' about any proprietary music, movies, or software, or enjoy same in the company of anyone other than themselves." RIAA attorneys said they were also looking into the legality of word-of-mouth "favorites-sharing" sites, such as coffee shops, universities, and living rooms.
Check out RIAA Bans Telling Friends About Songs from The Onion - America's Finest News Source, and a brilliant source of satire | digg story
Check out RIAA Bans Telling Friends About Songs from The Onion - America's Finest News Source, and a brilliant source of satire | digg story
Labels:
Music
What to do about Discovery?
My doctor friend who sent me the letter about Discovery raised some interesting observations. Some of these practices have been going on for some time. For example, if I buy a pair of prescription glasses for R1000, Discovery shows the claim of R1000 and deducts R1000 from my medical aid, but it only pays Torga Optical R850 because it is "entitled" to a 15% "settlement discount", AND it keeps the R150 that it deducted from my account.
 What do you do if you're a supplier? The choices are simple: make yourself unpopular with your clients by forcing them to pay you first, and then claim from Discovery after that, or claim from Discovery directly and lose out. But are these the only choices?
What do you do if you're a supplier? The choices are simple: make yourself unpopular with your clients by forcing them to pay you first, and then claim from Discovery after that, or claim from Discovery directly and lose out. But are these the only choices?
 The programmer in me says no. The programmer in me says that I should screw up Discovery's computer system by claiming the undiscounted amount, and keep on claiming until their system breaks.
The programmer in me says no. The programmer in me says that I should screw up Discovery's computer system by claiming the undiscounted amount, and keep on claiming until their system breaks.
 Here's how it works: the patient P goes to see the doctor D for a 1 hour consultation, which D charges at R200. When D sends the claim to the medical aid he is supposed to only claim R170. So D claims R200, and the claim is processed and pays out R170 to D. D then claims R30, which is then rejected, and the rejected amount shows on P's statement. Once the R30 is rejected, D claims the full R200, which is then rejected as a duplicate claim, and it appears on P's statement as a duplicate claim. Every month thereafter D claims the full R200 again, and each time the amount is rejected.
Here's how it works: the patient P goes to see the doctor D for a 1 hour consultation, which D charges at R200. When D sends the claim to the medical aid he is supposed to only claim R170. So D claims R200, and the claim is processed and pays out R170 to D. D then claims R30, which is then rejected, and the rejected amount shows on P's statement. Once the R30 is rejected, D claims the full R200, which is then rejected as a duplicate claim, and it appears on P's statement as a duplicate claim. Every month thereafter D claims the full R200 again, and each time the amount is rejected.
 Next time P comes to D, he is informed that he owes D R30 for the amount that Discovery didn't pay. Assuming that P visits D 3 times a year, by the end of the year there will be 4 paid claims, and around 22 duplicate or invalid claims, and D will be short by around R120. If D wanted to be unethical he could schedule an appointment that P doesn't keep, and claim another R170, which would cover the additional administration costs and interest. Or he could keep P waiting for longer than 1 hour and charge for 2 hours.
Next time P comes to D, he is informed that he owes D R30 for the amount that Discovery didn't pay. Assuming that P visits D 3 times a year, by the end of the year there will be 4 paid claims, and around 22 duplicate or invalid claims, and D will be short by around R120. If D wanted to be unethical he could schedule an appointment that P doesn't keep, and claim another R170, which would cover the additional administration costs and interest. Or he could keep P waiting for longer than 1 hour and charge for 2 hours.
 My doctor friend wouldn't do something that might be regarded as unethical, but it sure is tempting. I guess the best way to deal with Discovery is to buy shares in the company and raise a stink at the next shareholders' meeting. Perhaps I should do it for him.
My doctor friend wouldn't do something that might be regarded as unethical, but it sure is tempting. I guess the best way to deal with Discovery is to buy shares in the company and raise a stink at the next shareholders' meeting. Perhaps I should do it for him.
Tuesday, December 20, 2005
A medical doctor’s opinion of Discovery medical aid
Dear current or prospective medical aid member
 I, a doctor, write this email in the hope that it is circulated as far and wide as possible, to all those who are either members of Discovery medical aid plans, or who are thinking of joining. It is not my usual habit to do this, but the situation is becoming intolerable for the medical professional, and the consequences are bound to impact heavily on the public. This email offers reasons for why we doctors feel the way we do, and why we react negatively to medical aids in general, and to one in particular. Please, please take the time to read this through.
I, a doctor, write this email in the hope that it is circulated as far and wide as possible, to all those who are either members of Discovery medical aid plans, or who are thinking of joining. It is not my usual habit to do this, but the situation is becoming intolerable for the medical professional, and the consequences are bound to impact heavily on the public. This email offers reasons for why we doctors feel the way we do, and why we react negatively to medical aids in general, and to one in particular. Please, please take the time to read this through.
 Discovery Health is the largest player in the South African medical aid market, announcing a profit last year of R 563 million. In spite thereof Discovery management continues to disregard the needs and requests of the medical profession with regard to better professional fees, and has taken more and more of a destructive hand when it comes to interfering with the doctor-patient relationship. In business dealings and negotiations with the medical profession, Discovery management comes across as 'arrogant and inflexible.' In short we are dealing with a business bully who sees little need to address serious problems within the health sector relating to those who do all the work, i.e. medical doctors and paramedical services.
Discovery Health is the largest player in the South African medical aid market, announcing a profit last year of R 563 million. In spite thereof Discovery management continues to disregard the needs and requests of the medical profession with regard to better professional fees, and has taken more and more of a destructive hand when it comes to interfering with the doctor-patient relationship. In business dealings and negotiations with the medical profession, Discovery management comes across as 'arrogant and inflexible.' In short we are dealing with a business bully who sees little need to address serious problems within the health sector relating to those who do all the work, i.e. medical doctors and paramedical services.
 Discovery has alienated itself from the medical profession for the following reasons:
Discovery has alienated itself from the medical profession for the following reasons:
Blackmail tactics: Discovery will pay doctors directly, but only if accounts are submitted at much lower rates, even if the member is fully covered for private rates. So pressure is put on the doctor to charge a fee far less than deserved, for the 'privilege' of guaranteed payment. This is nothing else but blackmail. The reality is that members paid directly often spend the money elsewhere, leaving the doctor unpaid. Discovery Health knows this and uses this situation in an effort to cut their costs and maximise profits.
Low consultation rates: Discovery believes that a surgical specialist's rate for an hour consultation should be in the region of R170.00. Practices cost more than that to run. As such, this recognition of a service value below its cost promotes deterioration in patient care as doctors scramble to keep their practices running. For next year, Discovery management plans to pay out at 20% below the 'medical aid rate’ for some disciplines! Remember if you please last year's profit of R563 million. What on earth are they thinking?
Hospital rating system: Discovery has taken upon themselves the task of 'rating' private hospitals for procedures, arguing that this allows their members to 'choose better quality.' So one can look up a procedure at a hospital, and see it rated as 'poor,' 'below average, 'average,' or 'above average.' This rating system has been severely criticised for being biased and unscientific. It is misleading, of no use whatsoever to the member, and libelous to the doctors working in the clinics. Quality in medicine costs more, not less.
KeyCare package: This is a low cost Discovery medical aid plan marketed to those who cannot afford comprehensive medical aids. In principle, a good idea, but one can only go to certain hospitals, so the plan is of little use in towns or areas which do not have designated hospitals. The patient has no choice of specialist, and may have to travel to other towns for hospitalisation. The main issue is that the local doctor is expected to manage the pain and postoperative complications, without doing the initial surgery. One way we, as specialists, have decided to deal with this manipulation is by refusing to see patients on these plans coming to us solely because we work in a designated hospital. (For once doctors are starting to stick together.) The result however is that if you have a KeyCare plan, you may not be able to get the treatment you need because no doctor is prepared to treat you in another town. Moreover, brokers are now moving members from better plans onto this one, based on cost. The broker gets his commission, and the member gets a nasty shock. This practice is unethical.
Motivations: Nobody from a medical aid may refuse a surgical procedure or special test without discussing the case with the doctor on a peer-to-peer basis. From a medical aid point of view, this means that the medical advisor has to ring the doctor up and discuss the case with him. Medical advisors are accountable for their decisions, according to Health Profession Council rulings. The reality is that Discovery and other funds simply ignore this. They don't have enough medical advisors to speak personally to each doctor, and as a result they unilaterally make decisions affecting their member's health and refuse authorisations for tests or operations.
 What consequences will these bullying tactics have? Well, first of all, you are going to have to pay your doctor more out of your own pocket, over and above your increasing medical aid subscriptions, and probably at the time of service. (You pay your grocery, restaurant and petrol bills like this anyway, so it is probably a good thing.) Your relationship with your doctor may be at an instant disadvantage simply because of your medical aid. If you are on the KeyCare plan, you will not get the doctor you want, and may find the treatment you need is not available anywhere in your region. A third party, the medical advisor, is going become involved in every single decision affecting your treatment, able to deny investigations and quality treatment options, without the courtesy of discussing this with your doctor, and to date, without taking responsibility for your care should things go wrong.
What consequences will these bullying tactics have? Well, first of all, you are going to have to pay your doctor more out of your own pocket, over and above your increasing medical aid subscriptions, and probably at the time of service. (You pay your grocery, restaurant and petrol bills like this anyway, so it is probably a good thing.) Your relationship with your doctor may be at an instant disadvantage simply because of your medical aid. If you are on the KeyCare plan, you will not get the doctor you want, and may find the treatment you need is not available anywhere in your region. A third party, the medical advisor, is going become involved in every single decision affecting your treatment, able to deny investigations and quality treatment options, without the courtesy of discussing this with your doctor, and to date, without taking responsibility for your care should things go wrong.
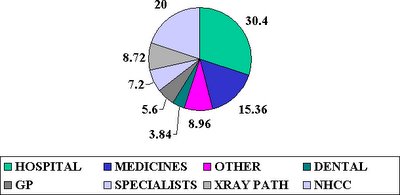
Where does my money go? It may surprise and shock you to know that of every rand you spend on medical aid, only 6 cents is spent on GP’s, and only 7 cents on medical specialists. The lion’s share of health expenditure (30.4%) goes to the hospitals, 15% on medications, 9% on radiologists and pathologists. Non-healthcare costs (NHCC) comprise 20% of the annual budget! This is what is spent on brokers’ commissions, and administration costs, more than all consulting doctors combined!
 There is a popular image of the doctor as a rich, money grabbing professional who puts his patient’s needs lower than that of his pocket. The reality is very different. For most doctors in this country, financial rewards are low on their lists of priorities. The truth is that practices are so expensive to run, and that medical practice in general comes with a list of responsibilities and sacrifices so great, that to struggle financially on top of it all makes us question why we put ourselves through all this effort in the first place. The answer is still what made us become doctors, a sense of responsibility to a noble calling. This responsibility, I believe, is what has prevented doctors from mobilising in the past. In a way it has become a weakness that others try to exploit.
There is a popular image of the doctor as a rich, money grabbing professional who puts his patient’s needs lower than that of his pocket. The reality is very different. For most doctors in this country, financial rewards are low on their lists of priorities. The truth is that practices are so expensive to run, and that medical practice in general comes with a list of responsibilities and sacrifices so great, that to struggle financially on top of it all makes us question why we put ourselves through all this effort in the first place. The answer is still what made us become doctors, a sense of responsibility to a noble calling. This responsibility, I believe, is what has prevented doctors from mobilising in the past. In a way it has become a weakness that others try to exploit.
 I hope the picture is starting to become clear. The public must ignore the advertising hype, the sporting sponsorships, and the mountaineering accomplishments, and realise what Discovery is doing to the medical profession. For the first time, there is a call for doctors to not see Discovery medical aid members for week. Call it, if you will, a strike. Nobody can refuse emergency treatment to a patient, but for non-urgent problems, that is a different story. I think it will be a sad day if this happens, but I speak for many medical professionals when I say that we have had enough of corporate greed and manipulation. I want the best technology, and the best outcome for my patient at a rate that is fair to me.
I hope the picture is starting to become clear. The public must ignore the advertising hype, the sporting sponsorships, and the mountaineering accomplishments, and realise what Discovery is doing to the medical profession. For the first time, there is a call for doctors to not see Discovery medical aid members for week. Call it, if you will, a strike. Nobody can refuse emergency treatment to a patient, but for non-urgent problems, that is a different story. I think it will be a sad day if this happens, but I speak for many medical professionals when I say that we have had enough of corporate greed and manipulation. I want the best technology, and the best outcome for my patient at a rate that is fair to me.
 So what can you do? I think at the very least you must write to Discovery and demand an explanation from them. The only way I see change happening is when the public vote with their feet, and move to another company. See your broker, and put this to him. There are many other medical aid plans that are far more supporting of the medical professional, and do not cost more.
So what can you do? I think at the very least you must write to Discovery and demand an explanation from them. The only way I see change happening is when the public vote with their feet, and move to another company. See your broker, and put this to him. There are many other medical aid plans that are far more supporting of the medical professional, and do not cost more.
 This link is very useful: http://www.health24.com/medical/Condition_centres/777-792-2002.asp. Alternatively email Discovery at healthinfo@discovery.co.za.
This link is very useful: http://www.health24.com/medical/Condition_centres/777-792-2002.asp. Alternatively email Discovery at healthinfo@discovery.co.za.
 Please forward this to as many people as you can, whether you are a Discovery member or not. Many other medical aids are influenced by their business tactics. If Discovery's power is not limited, all medical aids will one day be in this situation, with the member paying the consequences.
Please forward this to as many people as you can, whether you are a Discovery member or not. Many other medical aids are influenced by their business tactics. If Discovery's power is not limited, all medical aids will one day be in this situation, with the member paying the consequences.
 If so, it may not matter to we medical professionals, because at that time we may all (reluctantly) be in Canada.
If so, it may not matter to we medical professionals, because at that time we may all (reluctantly) be in Canada.
Name withheld for professional reasons
MBChB
FCS(SA)
Blackmail tactics: Discovery will pay doctors directly, but only if accounts are submitted at much lower rates, even if the member is fully covered for private rates. So pressure is put on the doctor to charge a fee far less than deserved, for the 'privilege' of guaranteed payment. This is nothing else but blackmail. The reality is that members paid directly often spend the money elsewhere, leaving the doctor unpaid. Discovery Health knows this and uses this situation in an effort to cut their costs and maximise profits.
Low consultation rates: Discovery believes that a surgical specialist's rate for an hour consultation should be in the region of R170.00. Practices cost more than that to run. As such, this recognition of a service value below its cost promotes deterioration in patient care as doctors scramble to keep their practices running. For next year, Discovery management plans to pay out at 20% below the 'medical aid rate’ for some disciplines! Remember if you please last year's profit of R563 million. What on earth are they thinking?
Hospital rating system: Discovery has taken upon themselves the task of 'rating' private hospitals for procedures, arguing that this allows their members to 'choose better quality.' So one can look up a procedure at a hospital, and see it rated as 'poor,' 'below average, 'average,' or 'above average.' This rating system has been severely criticised for being biased and unscientific. It is misleading, of no use whatsoever to the member, and libelous to the doctors working in the clinics. Quality in medicine costs more, not less.
KeyCare package: This is a low cost Discovery medical aid plan marketed to those who cannot afford comprehensive medical aids. In principle, a good idea, but one can only go to certain hospitals, so the plan is of little use in towns or areas which do not have designated hospitals. The patient has no choice of specialist, and may have to travel to other towns for hospitalisation. The main issue is that the local doctor is expected to manage the pain and postoperative complications, without doing the initial surgery. One way we, as specialists, have decided to deal with this manipulation is by refusing to see patients on these plans coming to us solely because we work in a designated hospital. (For once doctors are starting to stick together.) The result however is that if you have a KeyCare plan, you may not be able to get the treatment you need because no doctor is prepared to treat you in another town. Moreover, brokers are now moving members from better plans onto this one, based on cost. The broker gets his commission, and the member gets a nasty shock. This practice is unethical.
Motivations: Nobody from a medical aid may refuse a surgical procedure or special test without discussing the case with the doctor on a peer-to-peer basis. From a medical aid point of view, this means that the medical advisor has to ring the doctor up and discuss the case with him. Medical advisors are accountable for their decisions, according to Health Profession Council rulings. The reality is that Discovery and other funds simply ignore this. They don't have enough medical advisors to speak personally to each doctor, and as a result they unilaterally make decisions affecting their member's health and refuse authorisations for tests or operations.
Health Expenditure in the private sector in 2004

Where does my money go? It may surprise and shock you to know that of every rand you spend on medical aid, only 6 cents is spent on GP’s, and only 7 cents on medical specialists. The lion’s share of health expenditure (30.4%) goes to the hospitals, 15% on medications, 9% on radiologists and pathologists. Non-healthcare costs (NHCC) comprise 20% of the annual budget! This is what is spent on brokers’ commissions, and administration costs, more than all consulting doctors combined!
Name withheld for professional reasons
MBChB
FCS(SA)
Labels:
Consumer Complaints,
Discovery,
Rants
Monday, December 19, 2005
Web word processor adds PDF conversion
Web-based word processor Writely can now convert documents to the Real Text Format (RTF) and Adobe PDF standards, adding to recent new features like OpenDocument support.

read more | digg story

read more | digg story
Internet encyclopaedias go head to head
Wikipedia comes close to Britannica in terms of the accuracy of its science entries, a Nature investigation finds.
One of the extraordinary stories of the Internet age is that of Wikipedia, a free online encyclopaedia that anyone can edit. This radical and rapidly growing publication, which includes close to 4 million entries, is now a much-used resource. But it is also controversial: if anyone can edit entries, how do users know if Wikipedia is as accurate as established sources such as Encyclopaedia Britannica?
 Several recent cases have highlighted the potential problems. One article was revealed as falsely suggesting that a former assistant to US Senator Robert Kennedy may have been involved in his assassination. And podcasting pioneer Adam Curry has been accused of editing the entry on podcasting to remove references to competitors' work. Curry says he merely thought he was making the entry more accurate.
Several recent cases have highlighted the potential problems. One article was revealed as falsely suggesting that a former assistant to US Senator Robert Kennedy may have been involved in his assassination. And podcasting pioneer Adam Curry has been accused of editing the entry on podcasting to remove references to competitors' work. Curry says he merely thought he was making the entry more accurate.
 However, an expert-led investigation carried out by Nature — the first to use peer review to compare Wikipedia and Britannica's coverage of science — suggests that such high-profile examples are the exception rather than the rule.
However, an expert-led investigation carried out by Nature — the first to use peer review to compare Wikipedia and Britannica's coverage of science — suggests that such high-profile examples are the exception rather than the rule.
 The exercise revealed numerous errors in both encyclopaedias, but among 42 entries tested, the difference in accuracy was not particularly great: the average science entry in Wikipedia contained around four inaccuracies; Britannica, about three.
The exercise revealed numerous errors in both encyclopaedias, but among 42 entries tested, the difference in accuracy was not particularly great: the average science entry in Wikipedia contained around four inaccuracies; Britannica, about three.
 Considering how Wikipedia articles are written, that result might seem surprising. A solar physicist could, for example, work on the entry on the Sun, but would have the same status as a contributor without an academic background. Disputes about content are usually resolved by discussion among users.
Considering how Wikipedia articles are written, that result might seem surprising. A solar physicist could, for example, work on the entry on the Sun, but would have the same status as a contributor without an academic background. Disputes about content are usually resolved by discussion among users.
 But Jimmy Wales, co-founder of Wikipedia and president of the encyclopaedia's parent organization, the Wikimedia Foundation of St Petersburg, Florida, says the finding shows the potential of Wikipedia. "I'm pleased," he says. "Our goal is to get to Britannica quality, or better."
But Jimmy Wales, co-founder of Wikipedia and president of the encyclopaedia's parent organization, the Wikimedia Foundation of St Petersburg, Florida, says the finding shows the potential of Wikipedia. "I'm pleased," he says. "Our goal is to get to Britannica quality, or better."
 Wikipedia is growing fast. The encyclopaedia has added 3.7 million articles in 200 languages since it was founded in 2001. The English version has more than 45,000 registered users, and added about 1,500 new articles every day of October 2005. Wikipedia has become the 37th most visited website, according to Alexa, a web ranking service.
Wikipedia is growing fast. The encyclopaedia has added 3.7 million articles in 200 languages since it was founded in 2001. The English version has more than 45,000 registered users, and added about 1,500 new articles every day of October 2005. Wikipedia has become the 37th most visited website, according to Alexa, a web ranking service.
 But critics have raised concerns about the site's increasing influence, questioning whether multiple, unpaid editors can match paid professionals for accuracy. Writing in the online magazine TCS last year, former Britannica editor Robert McHenry declared one Wikipedia entry — on US founding father Alexander Hamilton — as "what might be expected of a high-school student". Opening up the editing process to all, regardless of expertise, means that reliability can never be ensured, he concluded.
But critics have raised concerns about the site's increasing influence, questioning whether multiple, unpaid editors can match paid professionals for accuracy. Writing in the online magazine TCS last year, former Britannica editor Robert McHenry declared one Wikipedia entry — on US founding father Alexander Hamilton — as "what might be expected of a high-school student". Opening up the editing process to all, regardless of expertise, means that reliability can never be ensured, he concluded.
 Yet Nature's investigation suggests that Britannica's advantage may not be great, at least when it comes to science entries. In the study, entries were chosen from the websites of Wikipedia and Encyclopaedia Britannica on a broad range of scientific disciplines and sent to a relevant expert for peer review. Each reviewer examined the entry on a single subject from the two encyclopaedias; they were not told which article came from which encyclopaedia. A total of 42 usable reviews were returned out of 50 sent out, and were then examined by Nature's news team.
Yet Nature's investigation suggests that Britannica's advantage may not be great, at least when it comes to science entries. In the study, entries were chosen from the websites of Wikipedia and Encyclopaedia Britannica on a broad range of scientific disciplines and sent to a relevant expert for peer review. Each reviewer examined the entry on a single subject from the two encyclopaedias; they were not told which article came from which encyclopaedia. A total of 42 usable reviews were returned out of 50 sent out, and were then examined by Nature's news team.
 Only eight serious errors, such as misinterpretations of important concepts, were detected in the pairs of articles reviewed, four from each encyclopaedia. But reviewers also found many factual errors, omissions or misleading statements: 162 and 123 in Wikipedia and Britannica, respectively.
Only eight serious errors, such as misinterpretations of important concepts, were detected in the pairs of articles reviewed, four from each encyclopaedia. But reviewers also found many factual errors, omissions or misleading statements: 162 and 123 in Wikipedia and Britannica, respectively.
Full story at news @ nature.com
One of the extraordinary stories of the Internet age is that of Wikipedia, a free online encyclopaedia that anyone can edit. This radical and rapidly growing publication, which includes close to 4 million entries, is now a much-used resource. But it is also controversial: if anyone can edit entries, how do users know if Wikipedia is as accurate as established sources such as Encyclopaedia Britannica?
Full story at news @ nature.com
Sunday, December 18, 2005
The Memory-Optimization Hoax
RAM optimizers make false promises
Mark Russinovich writes: "As you've surfed the Web, you've probably seen browser pop-ups such as "Defragment your memory and improve performance" and "Minimize application and system failures and free unused memory." The links lead you to utilities that promise to do all that and more for a mere $9.95, $14.95, or $29.95. Sound too good to be true? It is. These utilities appear to do useful work, but at best, RAM optimizers have no effect, and at worst, they seriously degrade performance.
 Literally dozens of so-called "memory optimizers" are available—some are commercial products and others are freeware. You might even be running such a product on your system. What do these products really do, and how do they try and fool you into thinking that they live up to their claims? Let's take a look inside memory optimizers to see exactly how they manipulate visible memory counters in Windows."
Literally dozens of so-called "memory optimizers" are available—some are commercial products and others are freeware. You might even be running such a product on your system. What do these products really do, and how do they try and fool you into thinking that they live up to their claims? Let's take a look inside memory optimizers to see exactly how they manipulate visible memory counters in Windows."
A while ago I found a free utility called PerfOptXP, that isn't a memory optimiser in the cateogry described by Mark, but rather a utility that allows you to tweak the settings on Windows so it works a bit better. Unfortunately the company that wrote it, WM Software, no longer distributes or supports it. But you can download it here (5,097,929 bytes), or from my free stuff page.
download it here (5,097,929 bytes), or from my free stuff page.
Read The Memory-Optimization Hoax | free stuff | WM Software
Mark Russinovich writes: "As you've surfed the Web, you've probably seen browser pop-ups such as "Defragment your memory and improve performance" and "Minimize application and system failures and free unused memory." The links lead you to utilities that promise to do all that and more for a mere $9.95, $14.95, or $29.95. Sound too good to be true? It is. These utilities appear to do useful work, but at best, RAM optimizers have no effect, and at worst, they seriously degrade performance.
A while ago I found a free utility called PerfOptXP, that isn't a memory optimiser in the cateogry described by Mark, but rather a utility that allows you to tweak the settings on Windows so it works a bit better. Unfortunately the company that wrote it, WM Software, no longer distributes or supports it. But you can
Read The Memory-Optimization Hoax | free stuff | WM Software
Labels:
Software
Saturday, December 17, 2005
Inmarsat Flips the Switch on First High-Speed Data Satellite
"UK-based satellite operator Inmarsat this week switched on the first of two satellites offering mobile voice and high speed IP data services in the latest stage of a six-year project costing 1.3 billion euros (US$1.6 billion).
 The project, dubbed Broadband Global Area Network (BGAN), is designed to provide both mobile voice and broadband data simultaneously, with guaranteed IP data rates on demand. The latest move follows on from the launch of two of the world's largest commercial satellites in March and November of this year.
The project, dubbed Broadband Global Area Network (BGAN), is designed to provide both mobile voice and broadband data simultaneously, with guaranteed IP data rates on demand. The latest move follows on from the launch of two of the world's largest commercial satellites in March and November of this year.
 Initially, BGAN will provide services across Europe, Africa, the Middle East and Asia, but following the activation of the operator's second satellite, services will be extended to North and South America in the second quarter of 2006.
Initially, BGAN will provide services across Europe, Africa, the Middle East and Asia, but following the activation of the operator's second satellite, services will be extended to North and South America in the second quarter of 2006.
 Ultimately, the two I-4 satellites will deliver broadband coverage across 85 percent of the world's landmass and 98 percent of the world's population, delivering IP data speeds of up to 492kbps, with guaranteed data rates up to 256kbps, potentially making it faster than 3G UMTS services.
Ultimately, the two I-4 satellites will deliver broadband coverage across 85 percent of the world's landmass and 98 percent of the world's population, delivering IP data speeds of up to 492kbps, with guaranteed data rates up to 256kbps, potentially making it faster than 3G UMTS services.
 Users would be able to browse the Web, use e-mail and stream video, audio and voice calls, all over a secure IP VPN connection, while the service launch is supported by a range of lightweight satellite terminals, similar in size to a standard laptop."
Users would be able to browse the Web, use e-mail and stream video, audio and voice calls, all over a secure IP VPN connection, while the service launch is supported by a range of lightweight satellite terminals, similar in size to a standard laptop."
At last, broadband without borders (and no Telkom!). I hate to imagine what it will cost, given how expensive Inmarsat phone calls are!
See Technology News: Networks : Inmarsat Flips the Switch on First High-Speed Data Satellite
At last, broadband without borders (and no Telkom!). I hate to imagine what it will cost, given how expensive Inmarsat phone calls are!
See Technology News: Networks : Inmarsat Flips the Switch on First High-Speed Data Satellite
Make remote shutdowns a cinch
"Eventually, all of us who manage computer networks need to reboot multiple computers as part of a maintenance task. The Windows Server 2003 or Windows XP Shutdown command and the Shutdown utility from the Microsoft Windows 2000 Server Resource Kit provide basic functionality but often fall short when dealing with shutdown variations on multiple remote computers. Sysinternals' PsShutdown, one of the tools in Sysinternals' free PsTools utility suite, offers more flexibility and power than the Microsoft Shutdown tools do. Plus, PsShutdown works on Windows NT 4.0 and later, although some options require Win2K or later."
Read Mark Russinovich's article, PsShutdown
Read Mark Russinovich's article, PsShutdown
Labels:
Software
RIAA Sued for Hacking
A WOMAN who was sued by the Recording Industry of America for file-sharing has countersued the outfit for hacking.
 Tanya Andersen, a 41-year old disabled single mother living in Oregon, has countersued the RIAA for Oregon RICO violations, fraud, invasion of privacy, abuse of process, electronic trespass, violation of the Computer Fraud and Abuse Act, negligent misrepresentation. She is claiming hurt feelings and "outrage", and deceptive business practices.
Tanya Andersen, a 41-year old disabled single mother living in Oregon, has countersued the RIAA for Oregon RICO violations, fraud, invasion of privacy, abuse of process, electronic trespass, violation of the Computer Fraud and Abuse Act, negligent misrepresentation. She is claiming hurt feelings and "outrage", and deceptive business practices.
 According to court documents here, Anderson said the record industry has been abusing the law courts and waged a public relations and public threat campaign targeting file sharing.
According to court documents here, Anderson said the record industry has been abusing the law courts and waged a public relations and public threat campaign targeting file sharing.
 She claims that the RIAA hired an outfit called MediaSentry to invade private home computers and collect personal information. Based on private information allegedly extracted from these personal home computers, the record companies have reportedly filed lawsuits against more than 13,500 anonymous "John Does".
She claims that the RIAA hired an outfit called MediaSentry to invade private home computers and collect personal information. Based on private information allegedly extracted from these personal home computers, the record companies have reportedly filed lawsuits against more than 13,500 anonymous "John Does".
 She claims the record companies provide the personal information to Settlement Support Center, which engages in outlawed and deceptive debt collection and other illegal conduct to extract money from the people allegedly identified from the secret lawsuits.
She claims the record companies provide the personal information to Settlement Support Center, which engages in outlawed and deceptive debt collection and other illegal conduct to extract money from the people allegedly identified from the secret lawsuits.
 She said that she has never downloaded or shared music online. She has not infringed on any of plaintiffs’ alleged copyrighted interest. However, she has been a victim of the record companies’ public threat campaign.
She said that she has never downloaded or shared music online. She has not infringed on any of plaintiffs’ alleged copyrighted interest. However, she has been a victim of the record companies’ public threat campaign.
 The RIAA falsely claimed that Andersen had been an "unnamed" defendant who was being sued in federal court in the District of Columbia. She was never named in that lawsuit and never received service of a summons and complaint, she said.
The RIAA falsely claimed that Andersen had been an "unnamed" defendant who was being sued in federal court in the District of Columbia. She was never named in that lawsuit and never received service of a summons and complaint, she said.
 When Andersen contacted Settlement Support Center, she was advised that her personal home computer had been secretly entered by the record companies’ agents, MediaSentry.
When Andersen contacted Settlement Support Center, she was advised that her personal home computer had been secretly entered by the record companies’ agents, MediaSentry.
 Apparently she had been up at 4:24am downloading "gangster rap" music under the login name “gotenkito@kazaa.com.” Andersen does not like "gangster rap", does not recognise the name "gotenkito", is not awake at 4:24 a.m. and has never downloaded music.
Apparently she had been up at 4:24am downloading "gangster rap" music under the login name “gotenkito@kazaa.com.” Andersen does not like "gangster rap", does not recognise the name "gotenkito", is not awake at 4:24 a.m. and has never downloaded music.
 The Settlement Support Center threatened that if Andersen did not immediately pay them, the record companies would bring an expensive and disruptive federal lawsuit using her name and they would get a judgment for hundreds of thousands of dollars.
The Settlement Support Center threatened that if Andersen did not immediately pay them, the record companies would bring an expensive and disruptive federal lawsuit using her name and they would get a judgment for hundreds of thousands of dollars.
 Looks like this one will run for a while.
Looks like this one will run for a while.
See The Inquirer: RIAA sued by victim | digg story | Blog index
See The Inquirer: RIAA sued by victim | digg story | Blog index
Friday, December 16, 2005
Hamachi: Stay Connected
With Hamachi you can organize two or more computers with an Internet connection into their own virtual network for direct secure communication.
 Access computers remotely. Use Windows File Sharing. Play LAN games. Run private Web or FTP servers. Communicate directly. Stay connected.
Access computers remotely. Use Windows File Sharing. Play LAN games. Run private Web or FTP servers. Communicate directly. Stay connected.
 Steve Gibson writes in the Security Now podcast/blog: "This week Leo and I discuss and describe the brand new, ready to emerge from a its long development beta phase, ultra-secure, lightweight, high-performance, highly-polished, multi-platform, peer-to-peer and FREE! personal virtual private networking system known as 'Hamachi'.
Steve Gibson writes in the Security Now podcast/blog: "This week Leo and I discuss and describe the brand new, ready to emerge from a its long development beta phase, ultra-secure, lightweight, high-performance, highly-polished, multi-platform, peer-to-peer and FREE! personal virtual private networking system known as 'Hamachi'.
 After two solid weeks of testing and intense dialog with Hamachi's lead developer and designer, I have fully vetted the system's security architecture and have it running on many of my systems. While I am travelling to Toronto this week, Hamachi is keeping my roaming laptop securely and directly connected to all of my machines back home. Don't miss this one!"
After two solid weeks of testing and intense dialog with Hamachi's lead developer and designer, I have fully vetted the system's security architecture and have it running on many of my systems. While I am travelling to Toronto this week, Hamachi is keeping my roaming laptop securely and directly connected to all of my machines back home. Don't miss this one!"
Listen to Security Now! #18: Hamachi rocks! | Hamachi Web site | digg story | Blog index
Listen to Security Now! #18: Hamachi rocks! | Hamachi Web site | digg story | Blog index
Labels:
Software
Ed gets it wrong, again!
I got an email today from Ed, the guy who claims to have hacked my PC using a "security flaw" in LimeWire. This time he's all excited about a "worm" (actually it's a trojan) that spreads using P2P programs, in this case LimeWire.
 The trojan is called Win32.Alcan.H and it poses as video.exe inside a ZIP file with the name of a porn movie. It also goes by the names of "W32.Alcra.D" or "Trojan-Dropper.Win32.WinAD.h". Yawn. There have been trojans like this around for as long as there have been P2P networks. A quick search on the Symantec virus encyclopedia lists 89 trojans that use LimeWire or related P2P networks.
The trojan is called Win32.Alcan.H and it poses as video.exe inside a ZIP file with the name of a porn movie. It also goes by the names of "W32.Alcra.D" or "Trojan-Dropper.Win32.WinAD.h". Yawn. There have been trojans like this around for as long as there have been P2P networks. A quick search on the Symantec virus encyclopedia lists 89 trojans that use LimeWire or related P2P networks.
 Anyone who downloads an executable (in a ZIP file or not) and doesn't treat it with extreme suspicion is a fool. Even the LimeWire User Guide warns you about executables. And anyway, since when was a porn movie only 602,893 bytes long? There are plenty of bogus files out there, and the moral of the story is simple: if it seems too good to be true, it probably is. Anyone who thinks they can download Office 2000 in 200k deserves the trojan/advert they get.
Anyone who downloads an executable (in a ZIP file or not) and doesn't treat it with extreme suspicion is a fool. Even the LimeWire User Guide warns you about executables. And anyway, since when was a porn movie only 602,893 bytes long? There are plenty of bogus files out there, and the moral of the story is simple: if it seems too good to be true, it probably is. Anyone who thinks they can download Office 2000 in 200k deserves the trojan/advert they get.
 It's sad that a company like Computer Associates can't tell the difference between a worm and a trojan, and it's sad that people like Ed don't read the virus alert properly anyway. But then Ed can't tell the difference between a security flaw and a product feature, or the difference between a "hidden" file and a non-existent one. But I guess when a "security consultant" like Ed plays fast and loose with the truth it's easy to lose perspective and fail to notice these details. Sad.
It's sad that a company like Computer Associates can't tell the difference between a worm and a trojan, and it's sad that people like Ed don't read the virus alert properly anyway. But then Ed can't tell the difference between a security flaw and a product feature, or the difference between a "hidden" file and a non-existent one. But I guess when a "security consultant" like Ed plays fast and loose with the truth it's easy to lose perspective and fail to notice these details. Sad.
 The only useful piece of information in the whole episode was the fact that the LimeWire sharing settings are stored in "limewire.props", a file stored in the
The only useful piece of information in the whole episode was the fact that the LimeWire sharing settings are stored in "limewire.props", a file stored in the
C:\Documents and Settings\user\.limewire
folder. Actually, I found a security issue there, which I have reported. No, Ed, it isn't a flaw, just a bad practice, and can't be used to hack anyone's machine.
Related pages: File not found; Flaw not found | Computer Assiciates "Worm" article | Go Ahead, Hack My LimeWire | Abort, Retry, Fail
C:\Documents and Settings\user\.limewire
folder. Actually, I found a security issue there, which I have reported. No, Ed, it isn't a flaw, just a bad practice, and can't be used to hack anyone's machine.
Related pages: File not found; Flaw not found | Computer Assiciates "Worm" article | Go Ahead, Hack My LimeWire | Abort, Retry, Fail
Subscribe to:
Posts (Atom)